Best 6 Software Supply Chain Security Solutions products
What is Software Supply Chain Security Solutions?
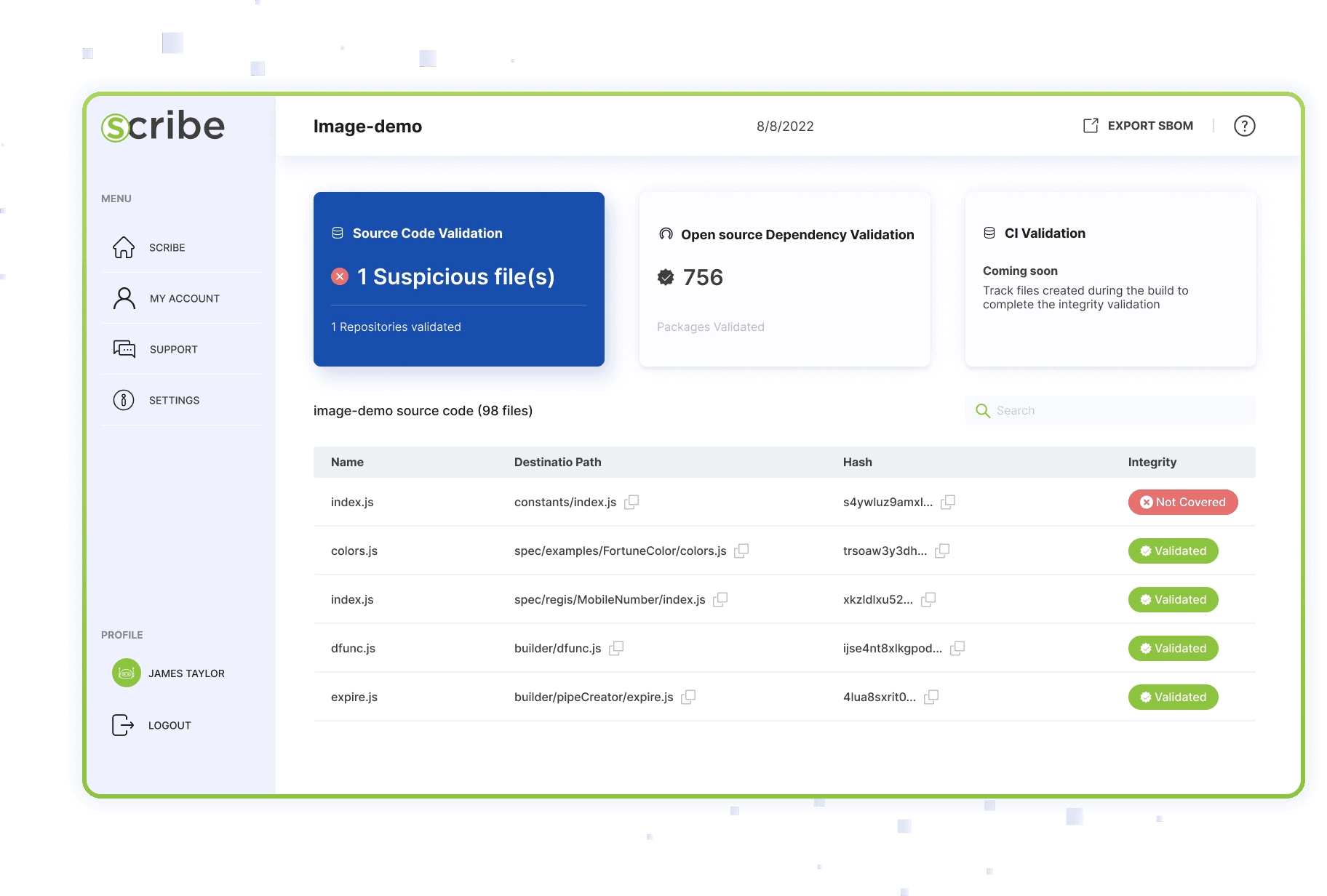
Software Supply Chain Security Solutions protect the software development and delivery process from risks like tampering, malware, and untrusted components by securing every stage from code creation to deployment.
What are the top 10 Development Software products for Software Supply Chain Security Solutions?
Newest Software Supply Chain Security Solutions Products
Software Supply Chain Security Solutions Core Features
- Component vulnerability scanning. Code integrity verification. Dependency management. Build environment security. Continuous monitoring and alerts
Advantages of Software Supply Chain Security Solutions?
- Prevents supply chain attacks. Enhances overall software integrity. Automates security checks. Reduces risk of breaches. Complies with industry regulations
Who is suitable to use Software Supply Chain Security Solutions?
Security teams, developers, DevOps engineers, and organizations concerned with protecting their software delivery pipeline from cyber threats.
How does Software Supply Chain Security Solutions work?
These solutions analyze software components and dependencies for vulnerabilities, enforce policies for trusted components, and monitor build pipelines for suspicious activity. By integrating security checks into CI/CD processes, they help prevent compromised code from reaching production.
FAQ about Software Supply Chain Security Solutions?
What is a software supply chain attack?
It's when attackers target parts of the software development or delivery process to insert malicious code.
How do these tools detect vulnerabilities?
They scan code and dependencies against known vulnerability databases and monitor for unusual activity.
Are they hard to integrate with existing workflows?
Most are designed to plug into popular CI/CD pipelines with minimal disruption.
Do these solutions cover open source components?
Yes, managing open source vulnerabilities is a major focus of these tools.
Can they prevent insider threats?
They provide monitoring and policy enforcement that can help reduce insider risks.